03 Apr 2020
Virus Total is a website that provides free service to evaluate files adn scan them across different security vendor’s products. We are able to upload files, add urls or IPs into the search bar and this will be searched across all security vendors and results are shown in the form of a report.This post and many to come are the activities which were done by me as a knowledge transfer sessions for my team while setting up an MSSP to provide SOC sesrvices to our various clients in Saudi Arabia.
VERIFY IP / HASH / DOMAIN NAME
To check if the IP, hash or filename is malicious or not, simply copy the IP/hash and paste it on the textbox in Virus total.
Open the Google Chrome Browser or any other prefered web browser, in the address bar type https://www.virustotal.com/ or click here.
Once the page loads, you should see something similar to this:
Note that there are three tabs,
- File: Use this option incase you have a malicious file and you’d like to see if it is malicious.
- URL: Select this Option if you have any URL that you have found in logs, or client has shared to see the reputation of the URL.
- Search: Select this tab, if you want to search for any IP, Hash or domain name to verify if this is malicious or a clean artifact.
EXAMPLE
- Copy the malicious IP using CTRL + C (from keyboard) or by using the mouse select the text of IP and make a right click and select Copy.
- Go to Google chrome browser or your preffered browser, in the address bar, make one left-click and type the following URL. https://www.virustotal.com
- Once the page has been loaded, click on the search tab in the middle of the page and wait for the text box to appear.
- In the search tab, paste the malicious IP copied in step 1, you can paste using CTRL + V (from keyboard) or use mouse to make one right-click and click paste.
- The end result would be as following except the IP mentioned is a dummy ip being used as an example.
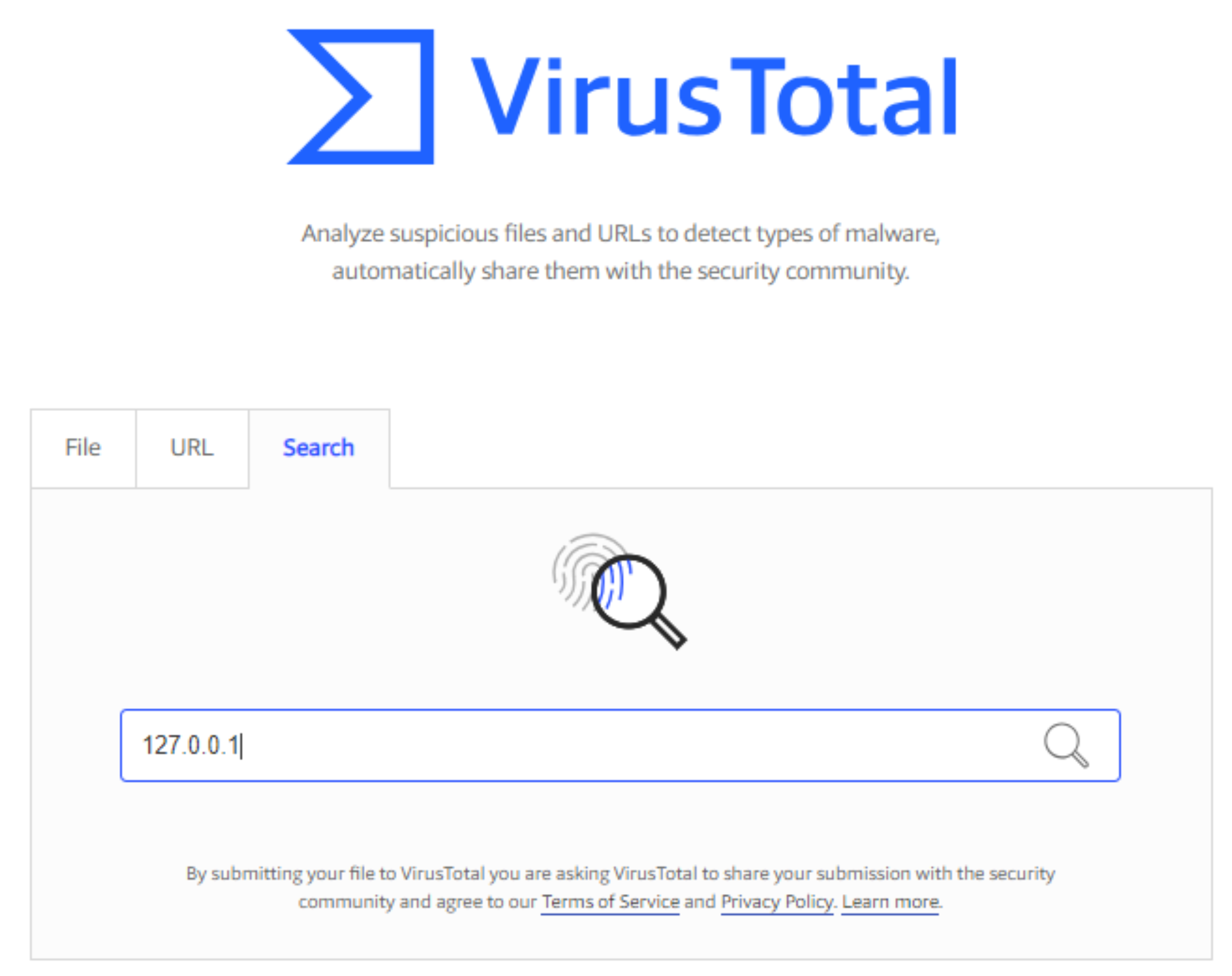
- Next click on the search icon (magnifier glass icon) at the right end of the textbox visible on the page.
- Wait for the page to load itself with results about the pasted IP.
- The result page would either report it as malicious or clean in the following way.
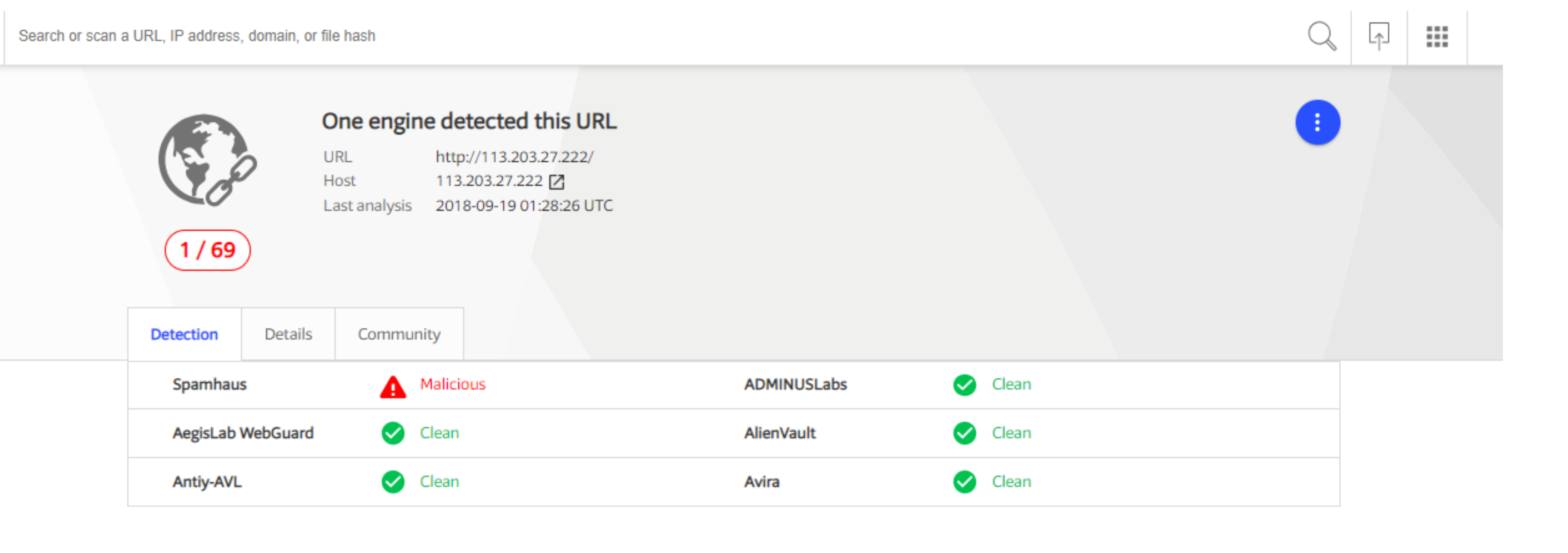
- Even if one of the engine’s mentioned in the result report it as malicious, we will share with client the remedial steps.
- If all the engine’s mention ‘Clean’ next to their name as visible for some of the engines in above picture, it can be considered as safe.
01 Feb 2020
One of my goals in 2019 was to read the DevOps book “The Phoenix Project” again to review the book and grasp the ideas in a better way, Last time, I had read this book was during my Master when main objective was to get done with the course requirements rather than actually understanding what is it about. This is a great novel which revolves around a project with many challenges popping up on the go and an organizational culture which is in a chaos.
This book successfully takes into account the critical issues faced by operations and development teams while also touching the key areas such as the importance of mapping between business requirements and information technology as an enabler of business.
I am just shortlisting few of the lessons that I have notices one can get from reading this book, however I’ll highly recommend to read this book for someone who is in operations or development teams.
IT as Enabler:
Information technology has successfully made its place to the critical areas of an organization within no time, with all business focusing toward business automation, quick communications, meeting supply and demand etc. IT has a role of an enabler of the business within any organization. If the IT department isn’t strong and is unable to meet the business requirements rapidly, you have a need to revisit your operational strategy. It is important to mention that IT and business both have to be on same side of the table to understand each other’s concerns and serve the customers in the best way possible.
Business Requirements:
Business department brings in most of the revenue unlike IT departments which is seen as a just a cost for business with no visible ROI in terms of numbers (Unless your business model is all IT oriented). All the supporting departments have to cater the business unit, by understanding the business goals and objectives clearly and work together to achieve the same goals. Business on the other hand, has to be clear on its requirements and pain points which it should share more openly with relevant stakeholders to come to a common workable way forward.
Scope:
This goes without saying that with no clear scope of a project, it is confirmed heading towards a failure. If any project is to be initiated, we need define the clear objectives and scope of the project to understand the requirements and identifying the relevant stakeholders. This has to trickle down in every task under any project to be very clear about the scope.
Change Management:
“Change is Constant” is something I truly believe in and is evident every day. With ever changing dynamics and customer trends, Business needs and operational requirements are bound to change. Change is to be braced head-on with a streamed process where the change gets prioritized based on certain criteria, approved and validated by all concerned stakeholders and properly scheduled before being implemented. The change management process, if streamlined, can bring down a large portion of production issues.
Speed of Delivery:
This is the key in this competitive arena. Without having the ability to deliver at the earliest Business has a bleak chance of success. This puts pressure on IT department to ensure that they have best practices in place which are followed properly for speedy deliverables. Business will always come with strange and yesterday-urgent requirements which have to be catered at a speed where we don’t lose our edge to competitors.
Jelled Team:
When people are put together in a team there are going to be conflicts which may turn into bigger issues, but given the time the same team comes to a mutual understanding when they learn more about each other, their roles and responsibilities and a common goal to attain. With clear responsibilities and goals to achieve, teams develop trust and respect among each other which helps them achieve wonder. Teams need to understand the concept of synergy which ensures that the effect of sum of all is great than the effect of all individually.
Three Ways:
This would be incomplete without mentioning the three ways which were mostly the focus of this book and are as follows:
Work Management:
Identifying the work is solving half the problem. There are 4 different types of work identified in this book which are very interesting to note:
-
Business Projects: All the projects which are addressing the business requirements. (New Campaign, New Website)
-
Internal Projects: All the projects which are run internally with in the operations team to enable the system to be operational. (e.g. Updates, Patches, regular maintenance)
-
Changes: All the requirements which are going to change how the system is operating.
-
Unplanned Work: All the tasks which are thrown at you due to any reason. (Server Crashed, System Functionality broke, troubleshooting issues.)
Be it any kind of work, standardizing the recurring tasks is something that should be one of the areas that need attention.
Security by Design:
One of the key areas which was evident is this book was that everyone viewed Information security department as an impediment in their progress. This is mainly because development department would usually consider the security requirements the least important and focus more the business needs itself to deliver the functional software. Another argument is the unnecessary requirements raised by the security department and making them all critical ensures that all requirements lose their importance. Security professionals need to realize that total security is not possible and aim should be to apply best possible controls that are required. Development and security teams have to work closely to implement the security needs within the design of the software instead of at a later stage where it gets very difficult to make changes.
Best Quote:
The book itself is filled with valuable lessons, however the best takeaway in my opinion is the following quote:
“Any improvement done at any place other than bottleneck is no improvement at all.”


